CSS Forums
Monday, May 06, 2024
08:47 PM (GMT +5)
08:47 PM (GMT +5)
|
|||||||
 |
Share Thread:
 Facebook
Facebook
 Twitter
Twitter
 Google+
Google+
|
|
|
LinkBack | Thread Tools | Search this Thread |
|
#1
|
||||
|
||||
|
Federal Public Service Commission Competitive Examination for Recruitment to Posts in BS-17 Under the Federal Government, 2013 Computer Science TIME ALLOWED: (PART-I) 30 MINUTES, MAXIMUM MARKS: 20 (PART-II) 2 HOURS & 30 MINUTES MAXIMUM MARKS: 80 Attempt ONLY FOUR questions from PART-II, selecting at least ONE question from EACH section. All questions carry EQUAL marks. PART-I (MCQs - COMPULSORY) 1. Which of the following best describes "virtual memory"? a. A portion of the hard disk considered as RAM. b. Extended memory on the secondary storage that is used whenever physical memory is full . c. The abstraction of separating logical memory - memory as seen by the process - from physical memory - memory as seen ny the processor. d. It is the page file in Windows folder. e. None of these. 2. The 'cmp' instruction modifies the: a. Instruction register. b. Flags register. c. Segment register. d. None of these. 3. Consider the following page reference string: 1,2,3,4,2,1,5,6,2,1,2,3,7,6,3,2,1,. Assuming there are 4 page framess available and that all frames are initially empty, what is the total number of page faults that would occur for the page reference string above if the least-recently-used (LRU) replacement policy is used? a. 6 b. 9 c. 10 d. 11 e. None of these 4. The Banker's algorithm is used to _________ a. Rectify deadlock b. Detect deadlock c. Prevent deadlock d. Avoid deadlock e. None of these 5. The necessary conditions needed before deadlock can occur are ________. a. No Mutual Exclusion, Hold and wait, Preemption, Circular Wait. b. Mutual Exclusion, No Hold and wait, Preemption, Circular Wait. c. Mutual Exclusion, Hold and wait, No Preemption, Circular Wait. d. Mutual Exclusion, Hold and wait, Preemption, No Circular Wait. 6. Differences between data lick layer and transport layer error detection is that: a. Data link detects transmission errors while transport layer detects segmentation faults. b. Data link detects node-to-node errors while transport layer detects end-to-end errors. c. Data link detects end-to-end errors while transport layer detects node-to-node errors d. Data link detects segmentation errors while transport layer detects bit error. e. None of theses 7. Phase Shift Keying (PSK) method is used to modulate digital signals at 9600bps using 16 levels. The line signals speed (i.e. modulation rate) will be: a. 1200 bands b. 2400 bands c. 4800 bands d. 9600 bands e. None of these 8. Exception handling is a powerful tenchnique that separates error-handling code from ______ code a. Buggy b. Faulty c. Normal d. Exceptional e. None of these 9. When a subroutine is called, the address of the instruction following the CALL instructions stored in/on the: a. Stack pointer b. Accumulator c. Programs counter d. Stack e. None of these 10. Binary tree "preorder" traversal is defined recursively as follows: a. Traverse left subtree, visit the root, traverse right subtree b. Traverse right subtree, visit the root, traverse left subtree c. Visit the root, traverse left subtree, traverse right subtree d. traverse left subtree, traverse right subtree, visit the root e. None of these 11. What value will return to the operating system upon the successful completion of a program? a. -1 b. 1 c. 0 d. None of these 12. Which of the following is TRUE about given UML diagram? 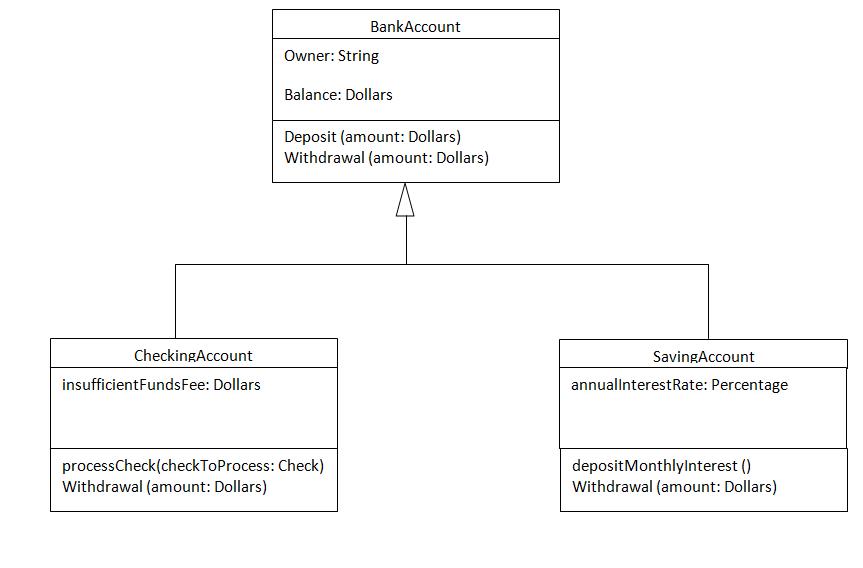 a. Checking Accound is a generalization of Saving Account b. Bank Account is composition of Checking Account and Saving Account c. Saving Account can process Check d. Checking Account has a balance? e. None of theses 13. The advantages of creating a prototype are: a. It allows developers to experiment with number of different design options. b. It can serve as means of communication between developers and customers. c. It is better than water fall model d. Both a and b e. None of these 14. Choose the correct statement: a. Testing can show the presence of bugs but never their absence b. Testing can always find all the bugs c. Testing can always be exhaustive d. If we test enough then we can find all of the bugs e. None of these 15. Which of the following operations need the participating relations to be union compatible? a. UNION b. INTERSECTION c. DIFFERENCE d. All of these e. None of these 16. The language used in application programs to request data from the DBMA is reffered to as the: a. DML b. DDL c. VDL d. SDL e. None of these 17. What is the correct XHTML for a paragraph? a. <P></p> b. <P></P> c. <p></p> d. </p><p> e. None of these 18. Which of the follwoing HTML form method is suitable when you need to send larger form submission? a. Get b. Post c. Both Get and Post d. Ajax e. None of these 19. (2,4) is a point on a circle that has senter at the origion. Which of the follwoing points are also on circle? a. (2,-4) b. (-2,4) c. (4,-2) d. All of the above e. None of these 20. In Bresenham's algorithm, while generating a circle, it is easy to generate? a. One octant first and other by successive reflection b. One octant first and other by successive rotation c. One octant first and other by successive translation d. All octants e. None of these. Attempt ONLY FOUR questions from PART-II, selecting at least ONE question from EACH section. All questions carry EQUAL marks. Part – II SECTION-A Q.2. (a) Define latency, transfer and seek time with respect to disk I/O. Compare given disk scheduling alorithm for cylinder requests in order 11, 1, 36, 16, 34, 9, 12: (8)
a. Semaphore b. Beledy's Anomlay c. Thrashing Q.3. (a) What is the significance of OSI model in communication paradigm/ Compare layers of OSI with TCP/IP protocol stack. (8) (b). Compare IEEE 802.3, IEEE 802.4 and IEEE 802.5? Also mention their problems and applications. (8) (c). Differentiate between Link State and Distance Vector routing protocols. (4) SECTION-B Q.4. (a) What is the concept of inheritance in OOP paradigm? How can we achieve inheritance in JAVA? (8) (b). Why is a B+ tree a better structure than an AVL tree for implementation of an indexed sequential file? Explain this with an example. (6) (c). Convert the expression ((A+B)*C-(D-E)^(F+G)) to equivalent Prefix and postfix notations. (6) Q.5. (a) describe the spiral model of software development with its application. (7) (b). Write a note on the following:
SECTION-C Q.6. (a) What are the main features of Relational data model? Why is it more useful than Hierarchical data model? (7) (b). What is 2PL? Give a schedule of two complete transactions that are not allowed by 'strict 2PL' scheduler but are accepted by basic 2PL scheduler. (7) (c). Write note on any ONE of the following: (6) a. ERD b. Normalization Q.7. (a) Why is the signicance of JavaScript in web development? Why is input validation done on client side? (5) (b). Explain any THREE of the following: (5 each = 15)
|
| The Following User Says Thank You to MisbahMalik For This Useful Post: | ||
Muhammad T S Awan (Saturday, March 09, 2013) | ||
 |
| Tags |
| computer science 2013, css 2013 |
«
Previous Thread
|
Next Thread
»
|
|
 Similar Threads
Similar Threads
|
||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| Falsifiability of science and transcendentlism of religion | sajidnuml | Essays | 1 | Wednesday, September 02, 2015 07:36 PM |
| A list of branches of Science and their studies | usman malik 65 | General Science Notes | 0 | Tuesday, July 13, 2010 11:23 AM |
| computers | wasikhan | General Science & Ability | 0 | Thursday, March 25, 2010 07:30 PM |






